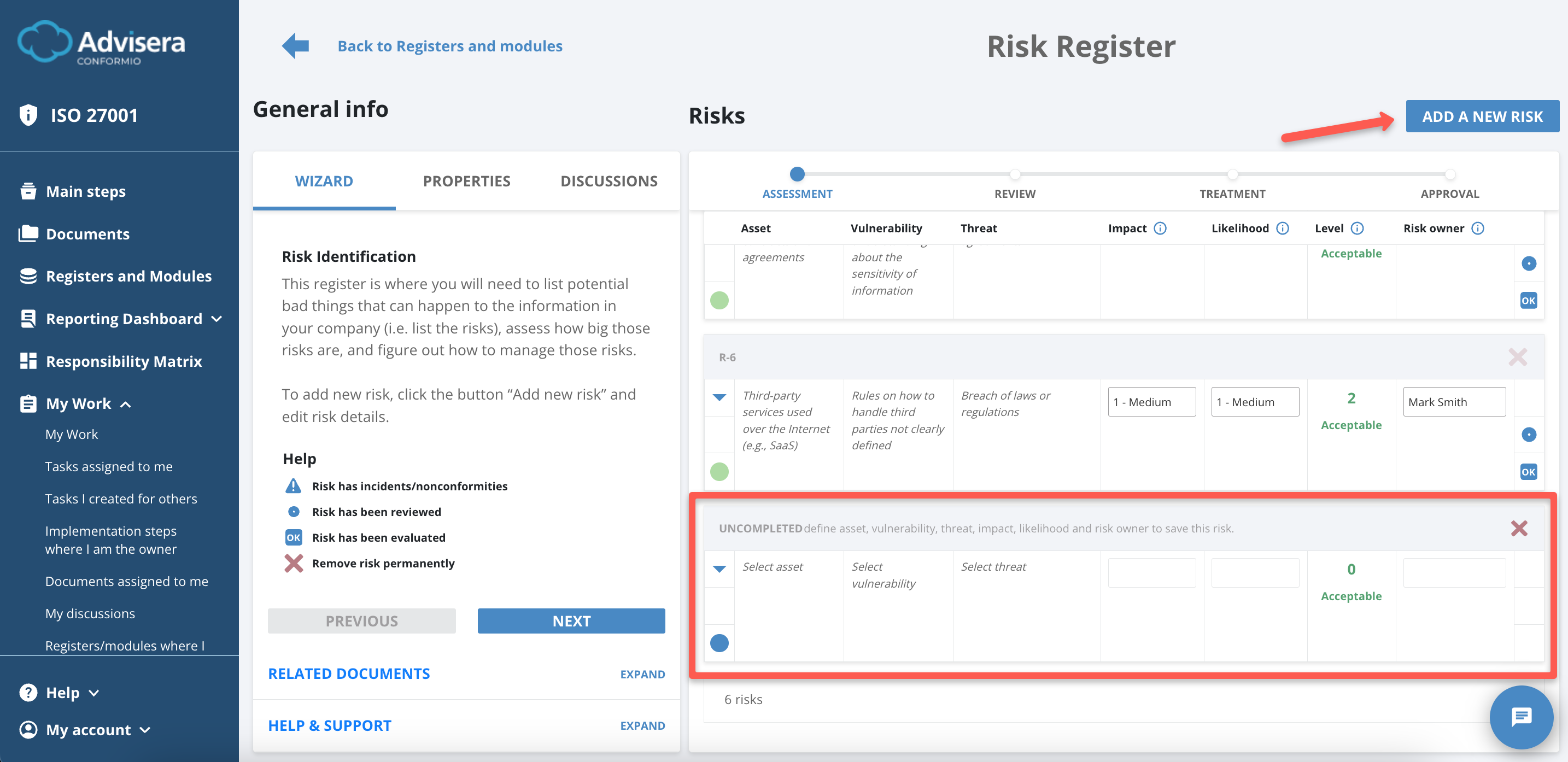
The Risk Register is a step you will complete as part of the Register and Modules. The Risk Register will provide a complete overview of the risks that are in your company. From physical to digital risks, all should be included. This register is the backbone of your ISO 27001 certification.
Accessing Risk Register
There are 2 ways to access the Risk Register:
- Through the Risk Register step in the Implementation steps;
- Through Registers and Modules.
Accessing through Risk Register Step
Follow these steps to access the Risk Register:
- Go to Compliance and select Implementation steps;
- Find the Risk Register and click on the step or the Arrow button;
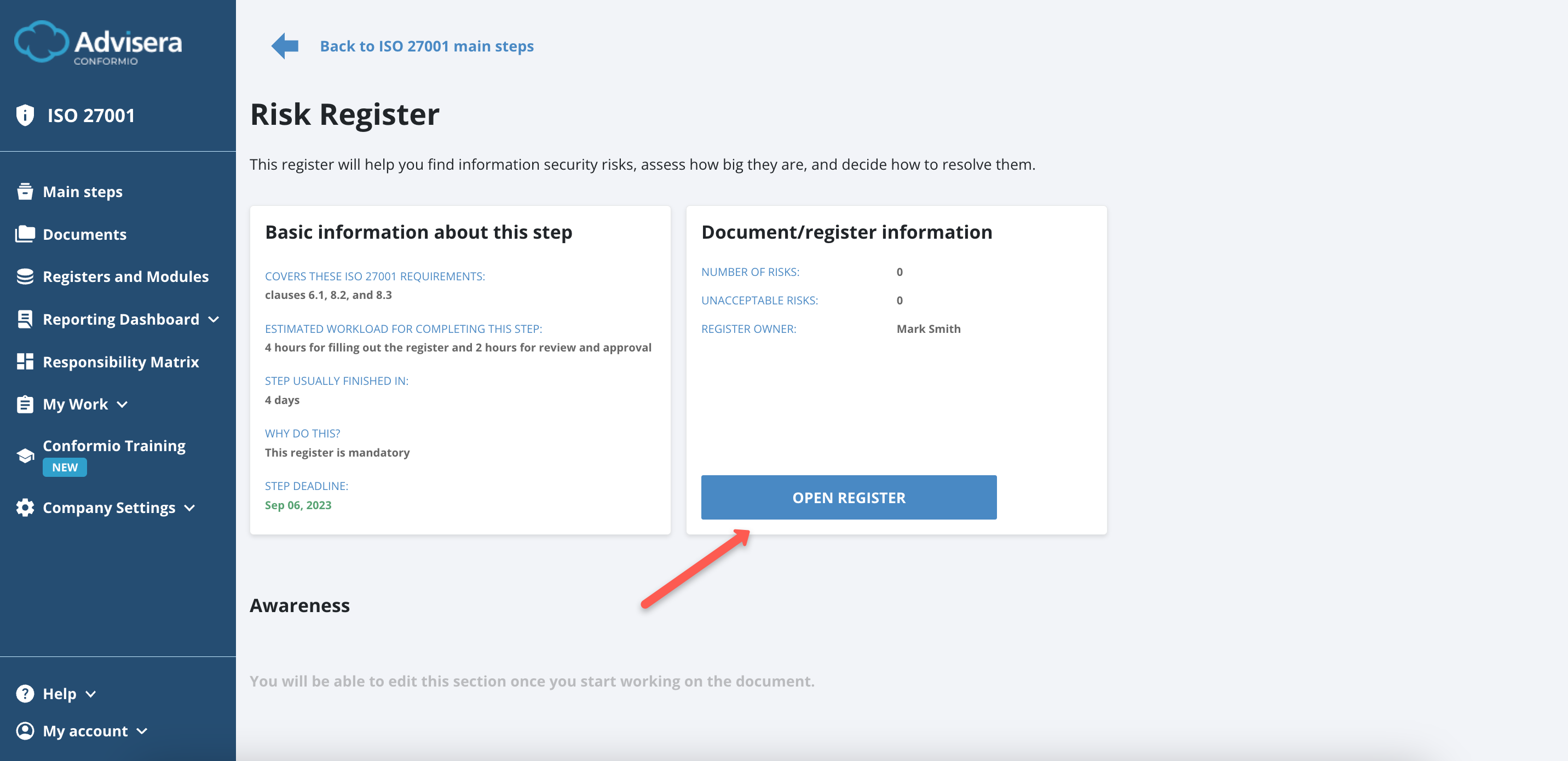
- From the step, click the Open Register button.
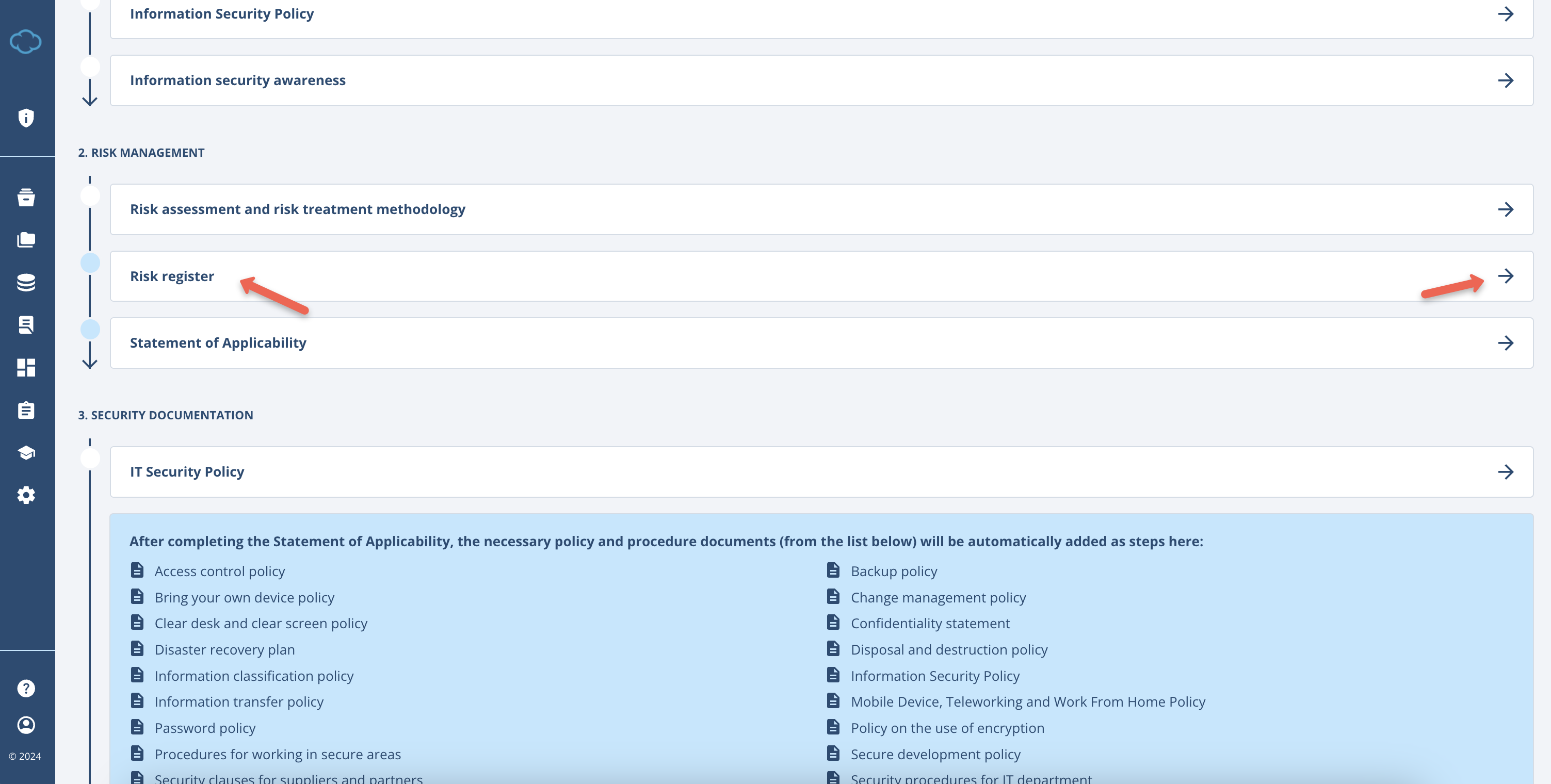
Accessing through Registers and Modules
Follow these steps to access the Risk Register:
- Click on Registers and Modules in the menu;
- Click the Go To Register button on the Risk Register module.
Risk Register Overview
The Risk Register is divided into the following sections:
- Assets;
- Vulnerabilities;
- Threats;
- Evaluation;
- Review;
- Treatment;
- Approval.
Assets
Assets are divided into the following categories:
- Infrastructure;
- IT & Communication Equipment;
- Software & Databases;
- Other Documents and data;
- Human Resources;
- Third-party Services.
Conformio suggests up to 30 assets based on the company size Conformio is aimed for (Small and Medium-sized Enterprises). You can select more assets if needed.
Type of Assets
You should include only the assets that you directly control. Those are the assets which you can directly set the security rules for.
|
Examples You can include the following assets in your ISMS Scope:
You should not include the following assets in your ISMS Scope:
|
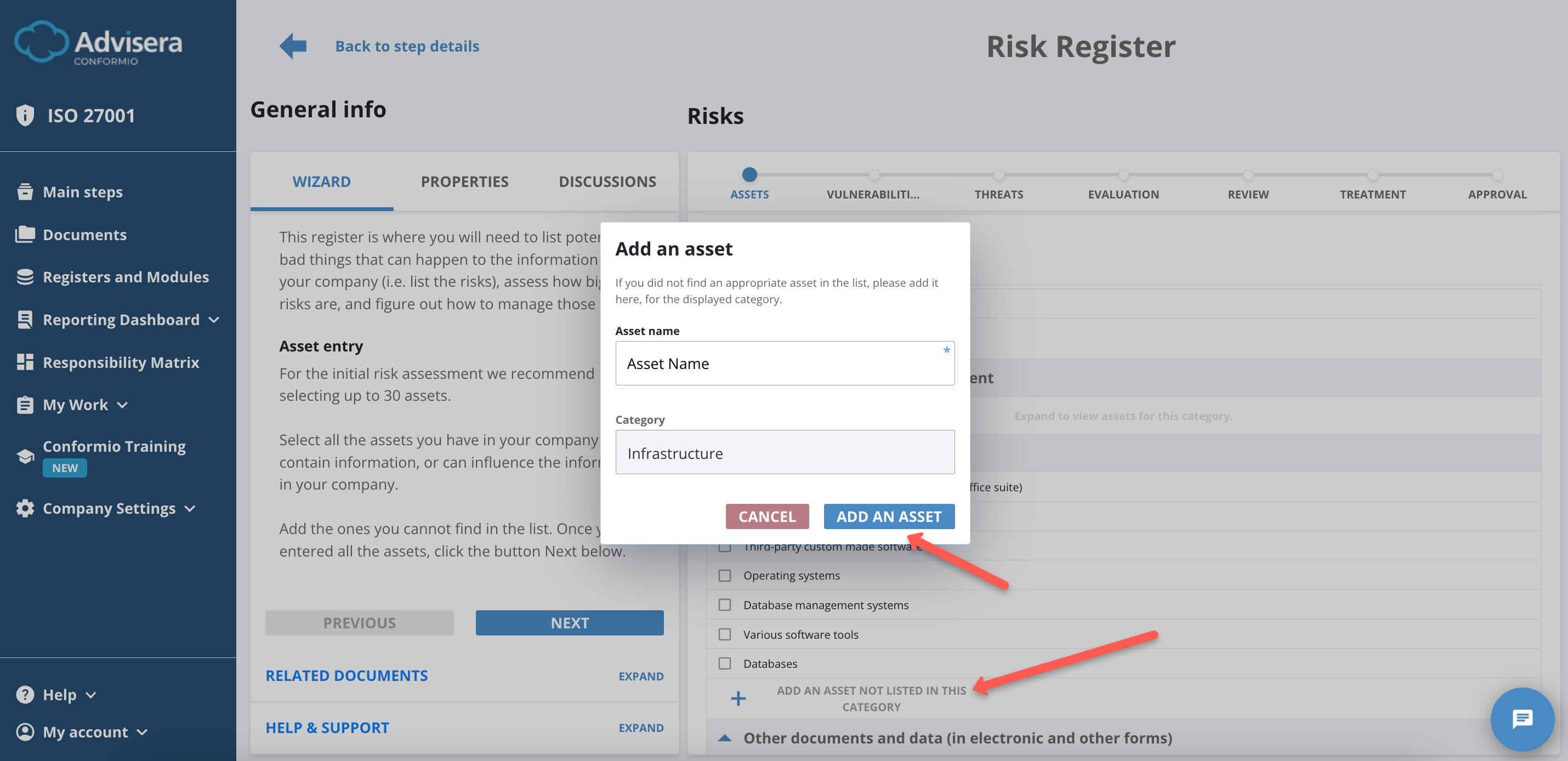
Creating Assets
If you have an asset not already listed, you can create your own under the provided categories.
To create an asset, do the following:
- Click the Add an Asset Not Listed in This Category button;
- Enter all information;
- Click the Add an Asset button.
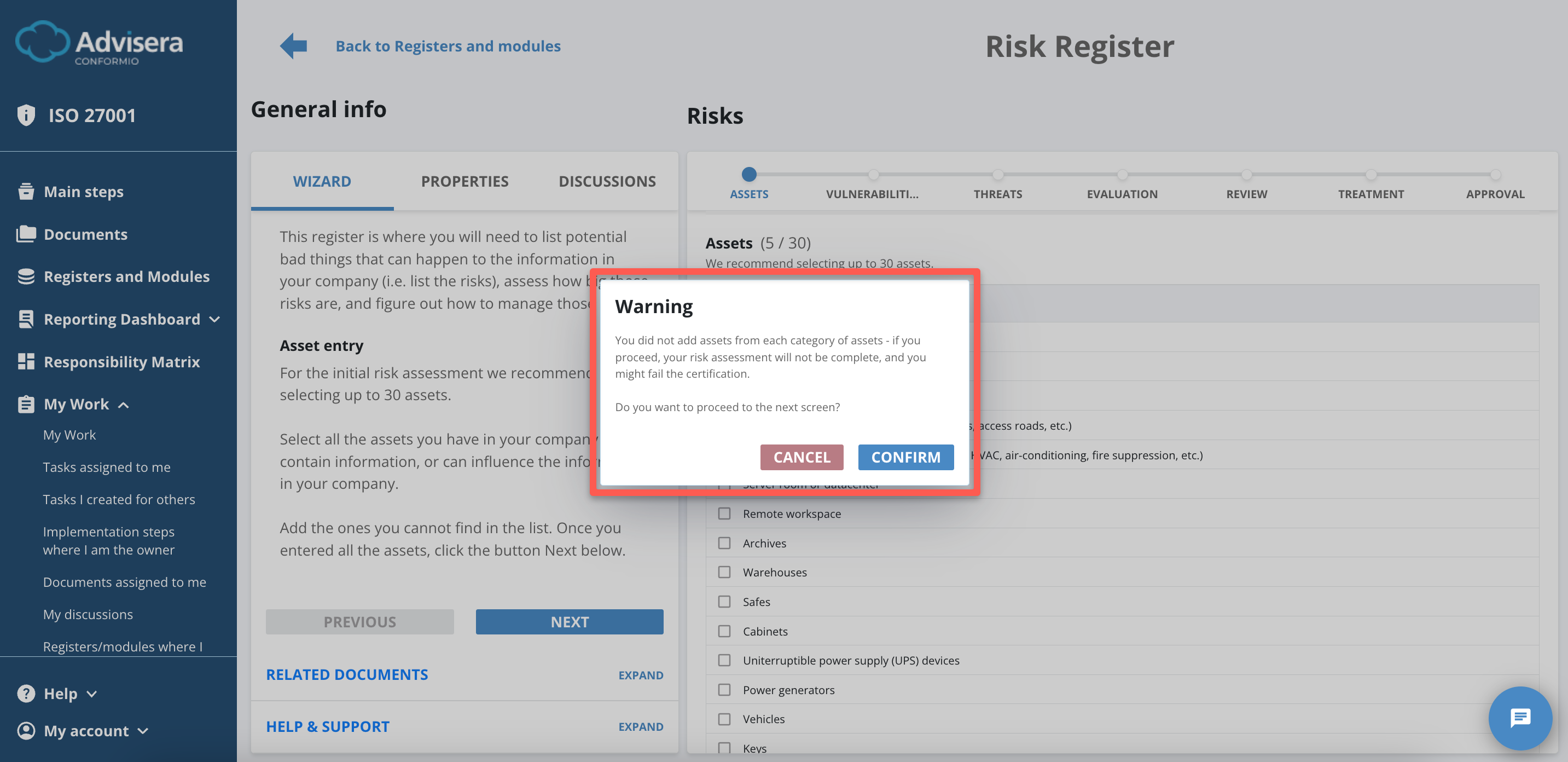
You must select at least one asset in each category to proceed to Vulnerabilities by clicking the Next button.
If there is an empty category of assets, the error message appears where you can proceed, but with the risk of failing certification.
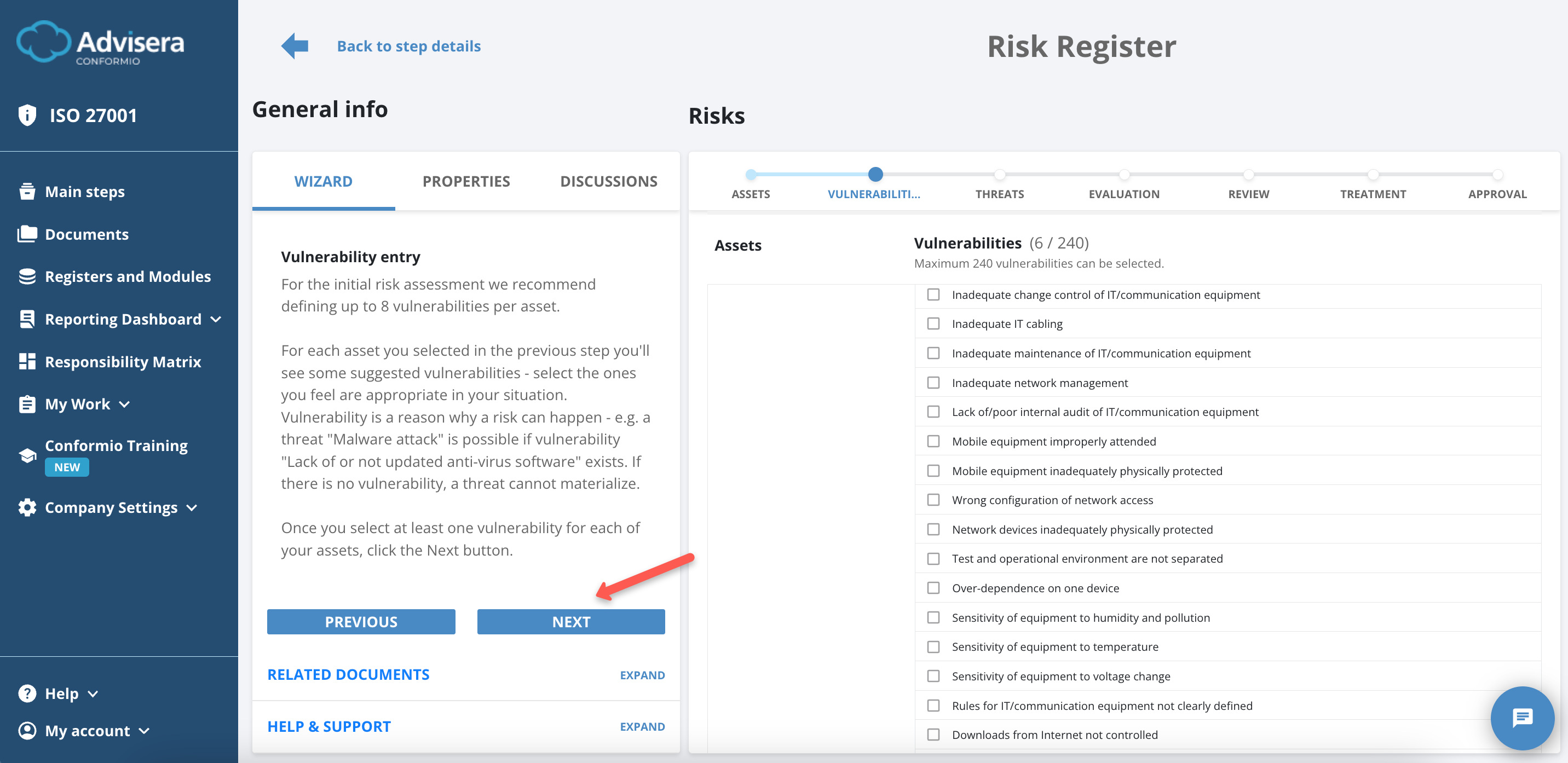
Vulnerabilities
You need to provide a vulnerability for every selected asset in the previous selection screen. Conformio suggests several possible vulnerabilities. If a vulnerability is specifically occurring in your company but is not on the Conformio list, you can create it.
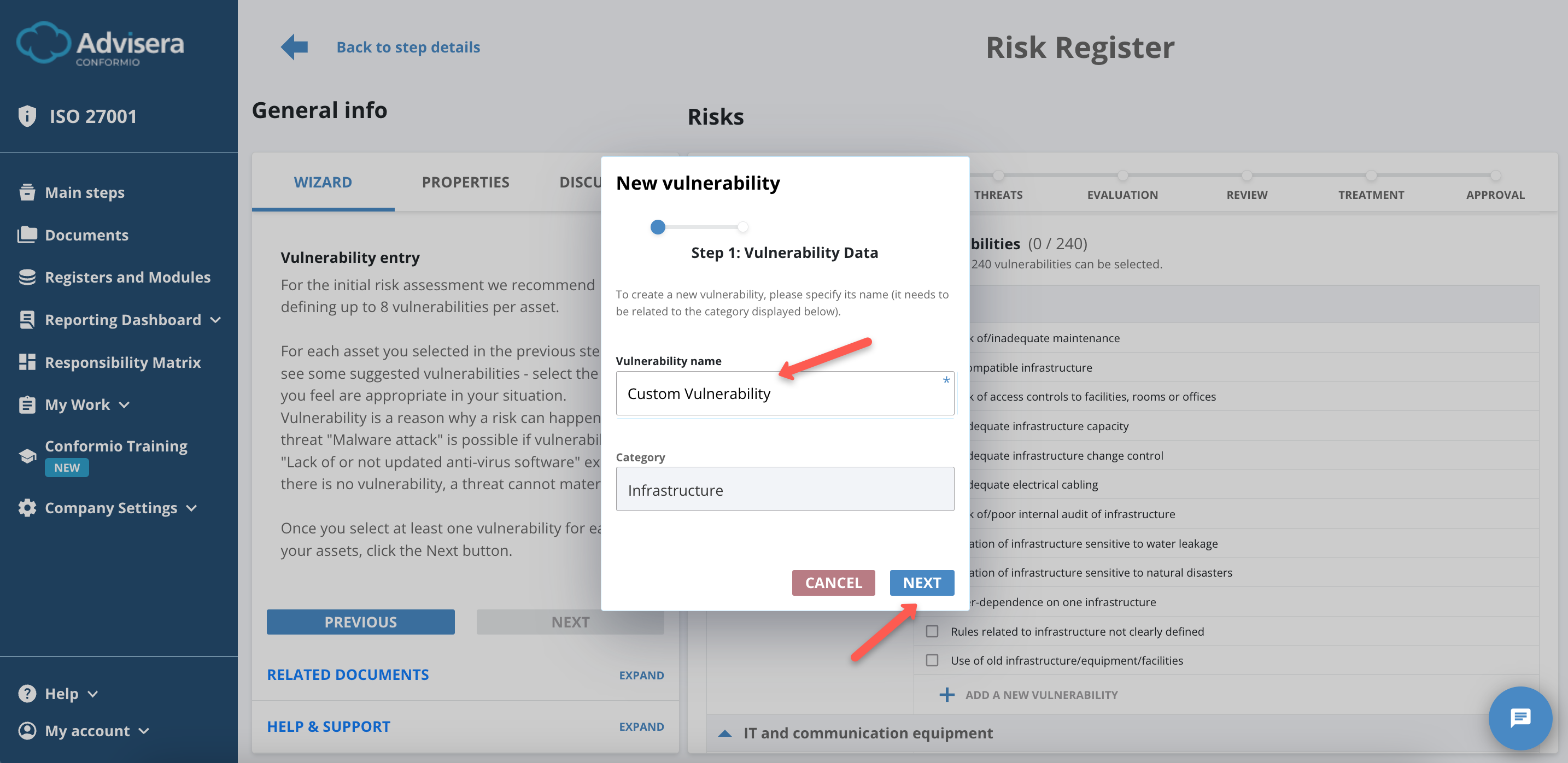
Creating Vulnerabilities
To create a vulnerability, do the following:
- Click the Create a New Vulnerability at the end of the vulnerabilities’ list;
- Input vulnerability name and category;
- Click the Next button;
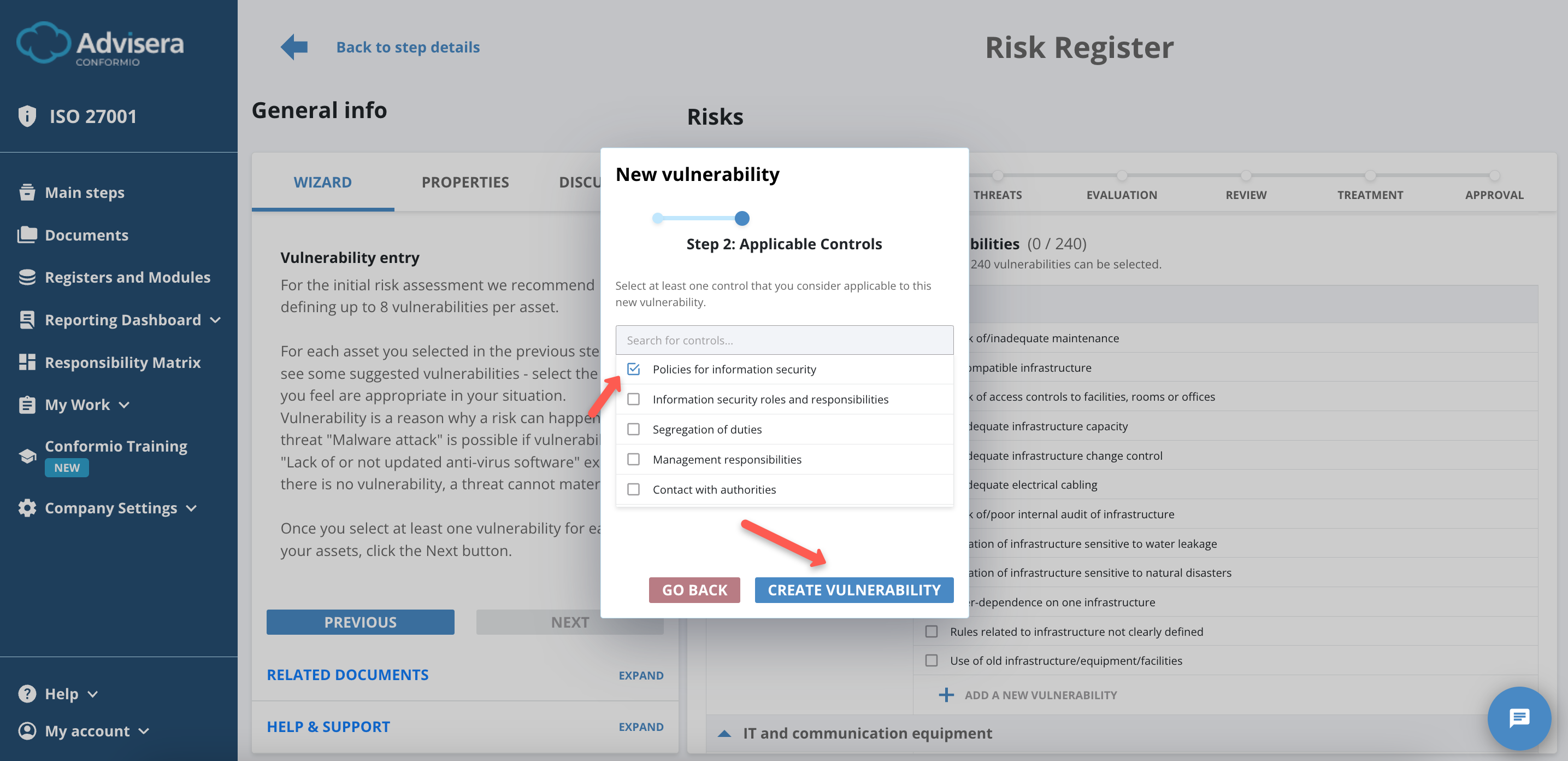
- Select Applicable Controls (at least 1);
- Click the Create Vulnerability button.
Conformio suggests up to 240 vulnerabilities based on the company size Conformio is aimed for (Small and Medium-sized Enterprises). You can select more assets if needed.
Type of Vulnerabilities
Threats and vulnerabilities are used to describe a risk that is related to a particular asset.
Vulnerability is a characteristic of an asset (e.g., a flaw or absence of protection) that allows a threat to materialize. It is always related to a particular asset.
A threat is a cause of a security incident (something bad that will happen) that exploits the vulnerability to damage the asset.
In other words, if there is no vulnerability, a threat cannot materialize. If there is no threat, then vulnerability cannot be exploited.
|
Examples
|
When all your vulnerabilities are successfully selected for each asset, click the Next button to proceed.
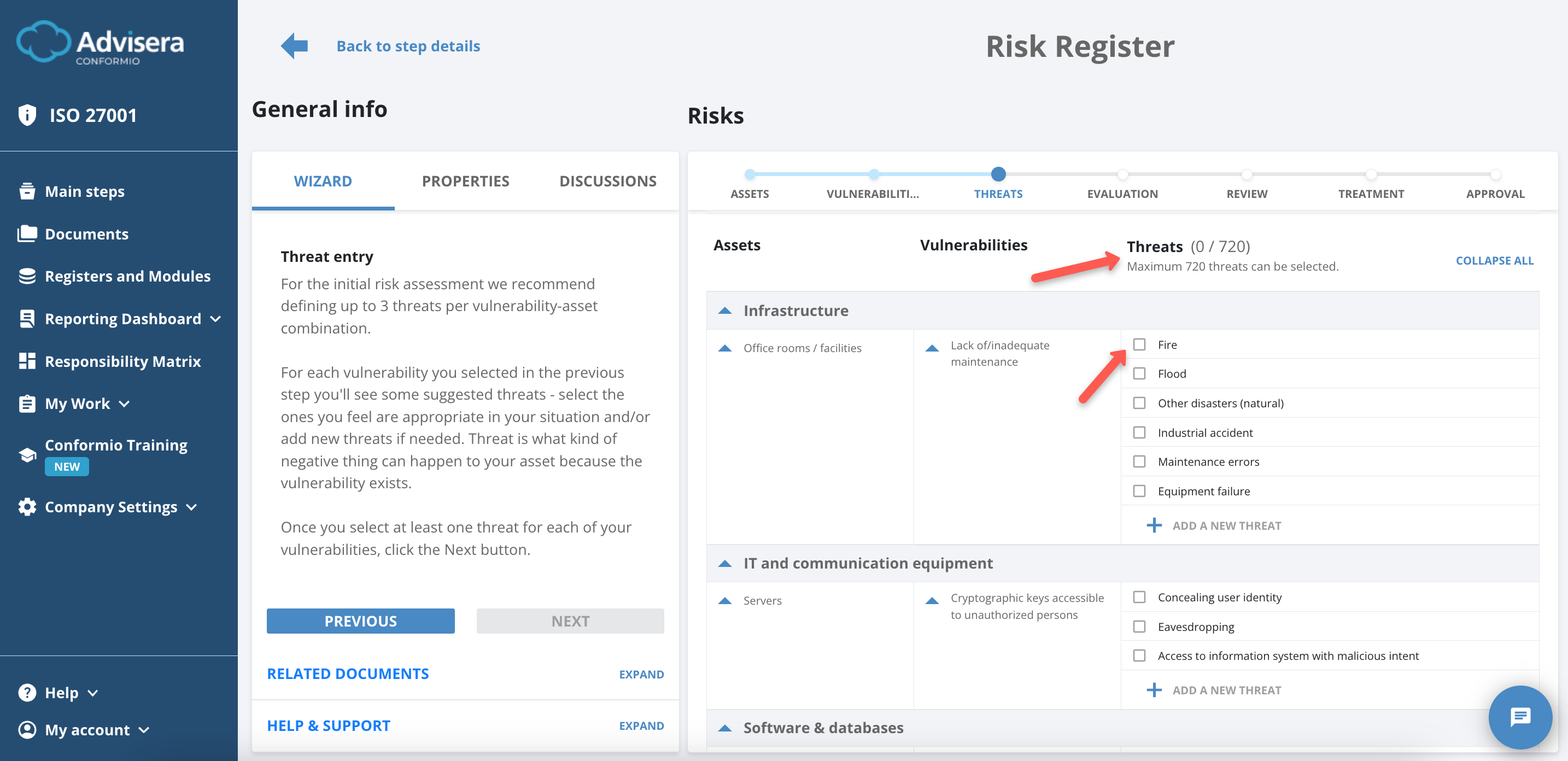
Threats
Risk Register defines what threats are connected to previously selected assets and vulnerabilities.
Conformio suggests up to 720 threats based on the company size Conformio is aimed for (Small and Medium-sized Enterprises). This will translate to 720 risks.
Matching Threats to Vulnerabilities
Vulnerabilities are related to particular assets, so when analyzing your assets, you should think through which characteristics of an asset (i.e., a flaw or lack of protection) will enable a threat to materialize.
Threats exploit those vulnerabilities, so you should consider what kind of bad things can happen to those assets – threats can be a force majeure, internal organizational oversight, unintentional human errors (malicious attacks or technical faults.)
|
Examples Asset – paper document:
Asset – digital document:
|
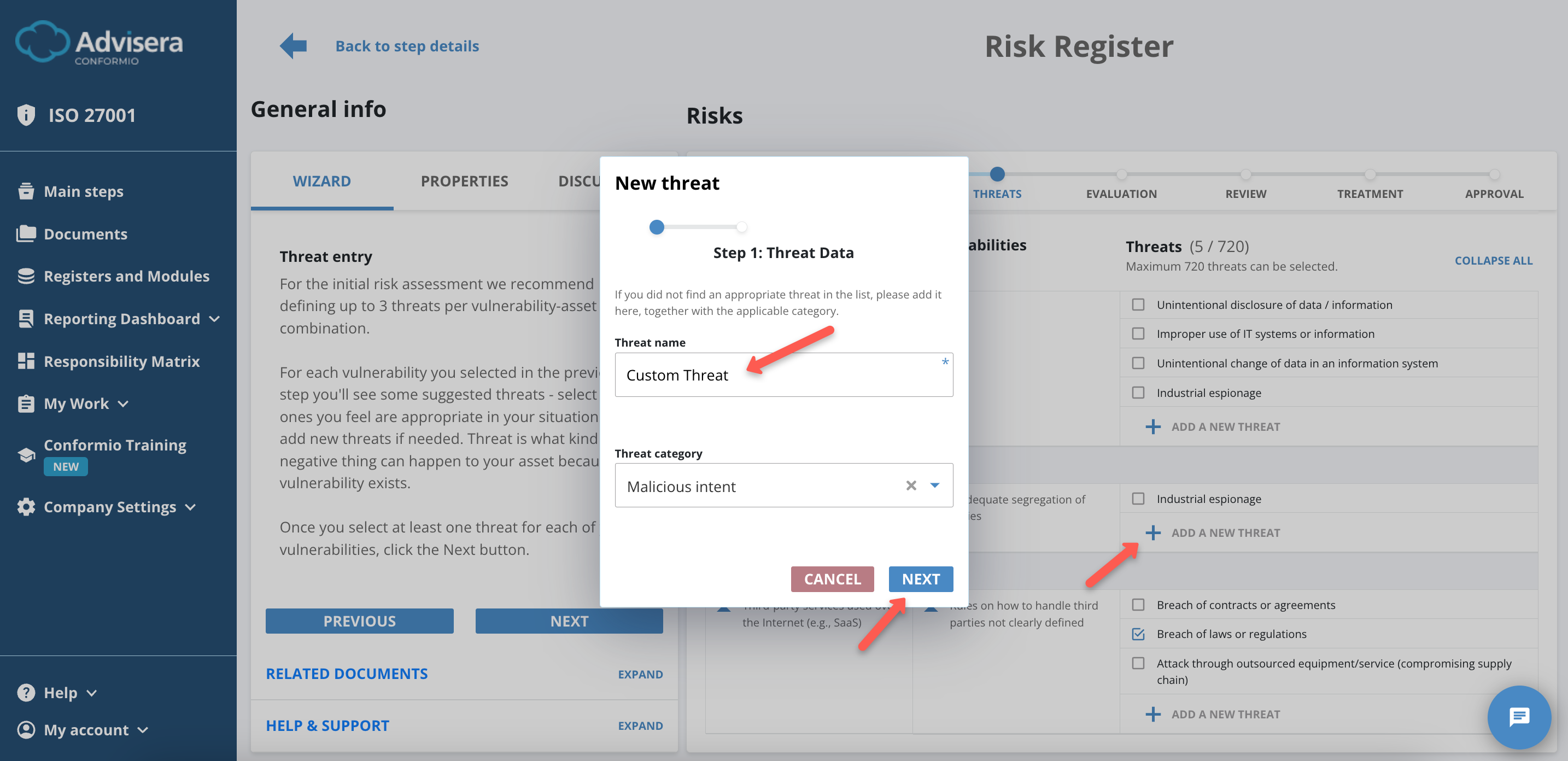
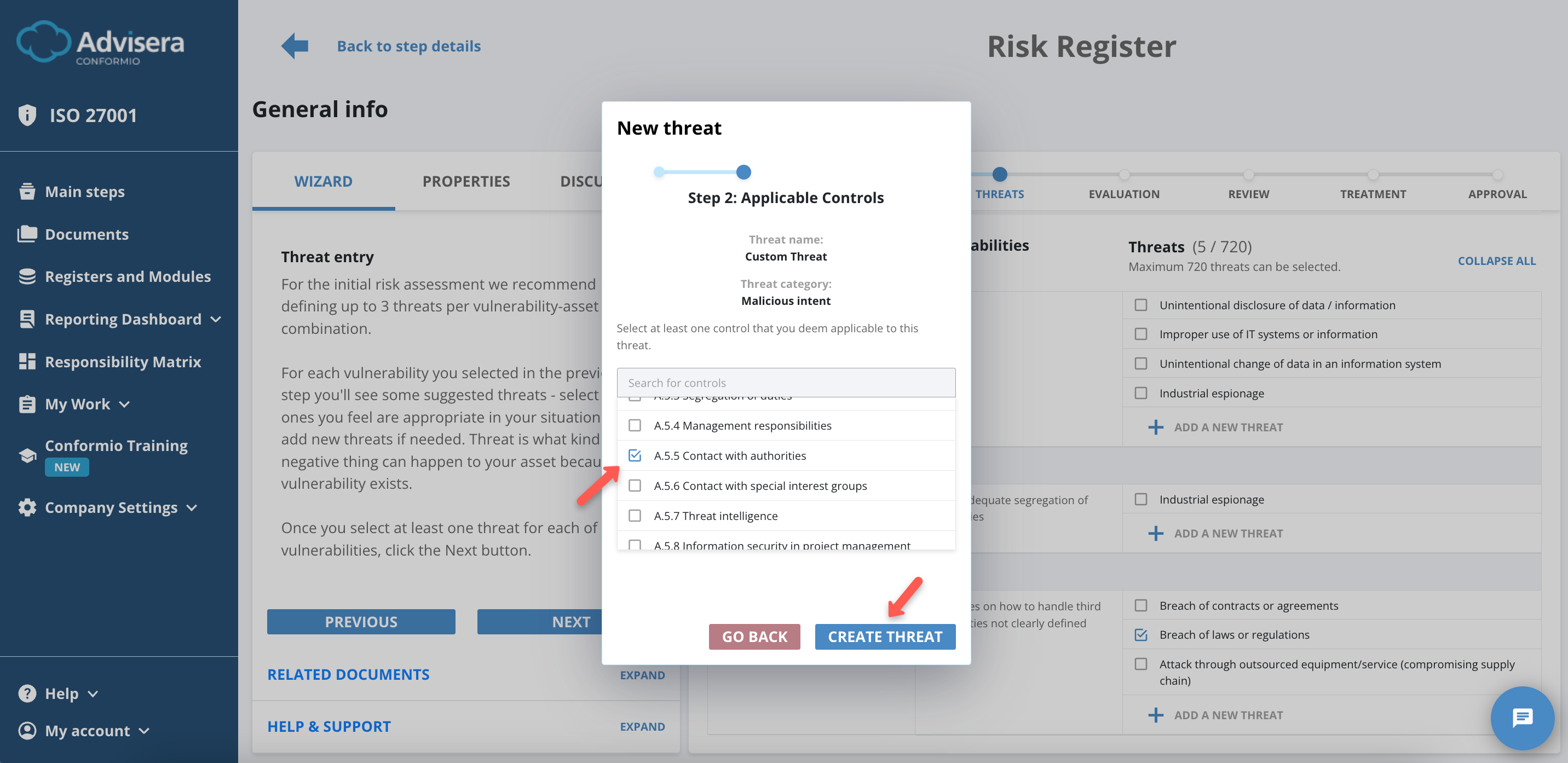
Creating Threats
If you have a threat not already listed, you can create your own.
To create a threat, do the following:
- Click the Add a New Threat at the end of the threats list;
- Input threat name and category;
- Click the Next button;
- Select Applicable Controls (at least 1);
- Click the Create Threat button.
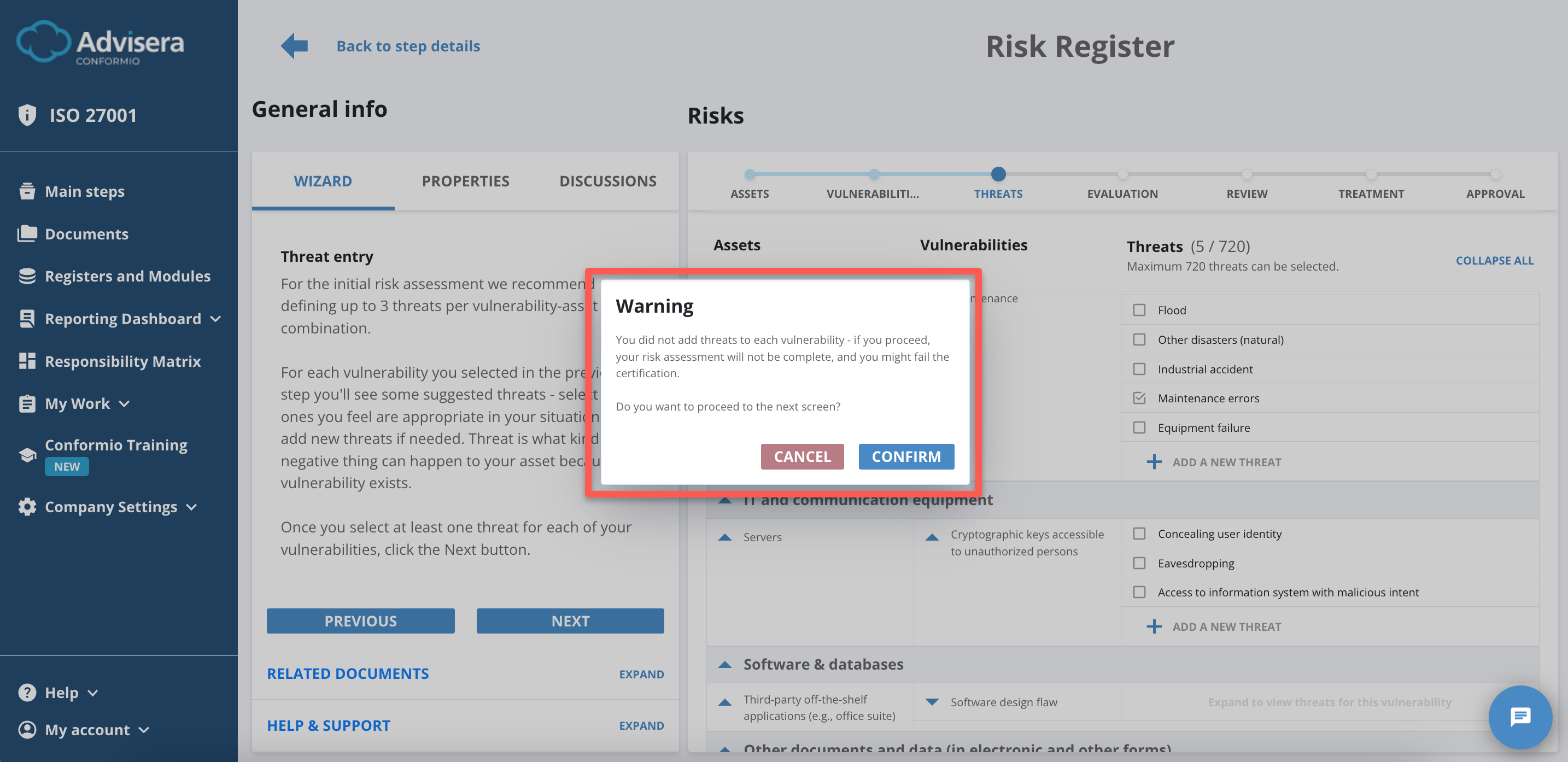
You must have at least one threat selected for each vulnerability and asset to proceed to Evaluation by clicking the Next button. Otherwise, you might have an incomplete risk assessment, which can be the reason you fail your certification.
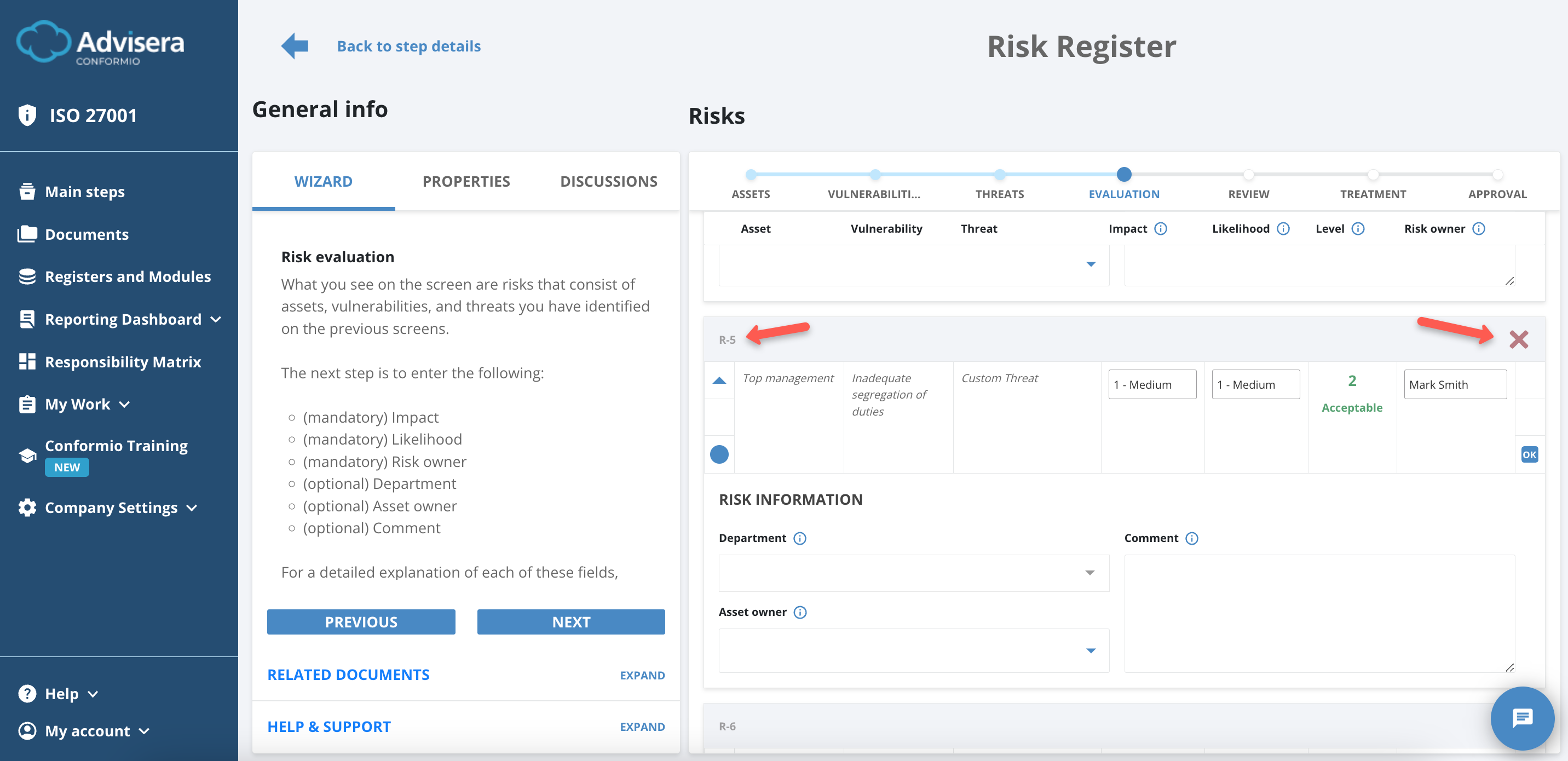
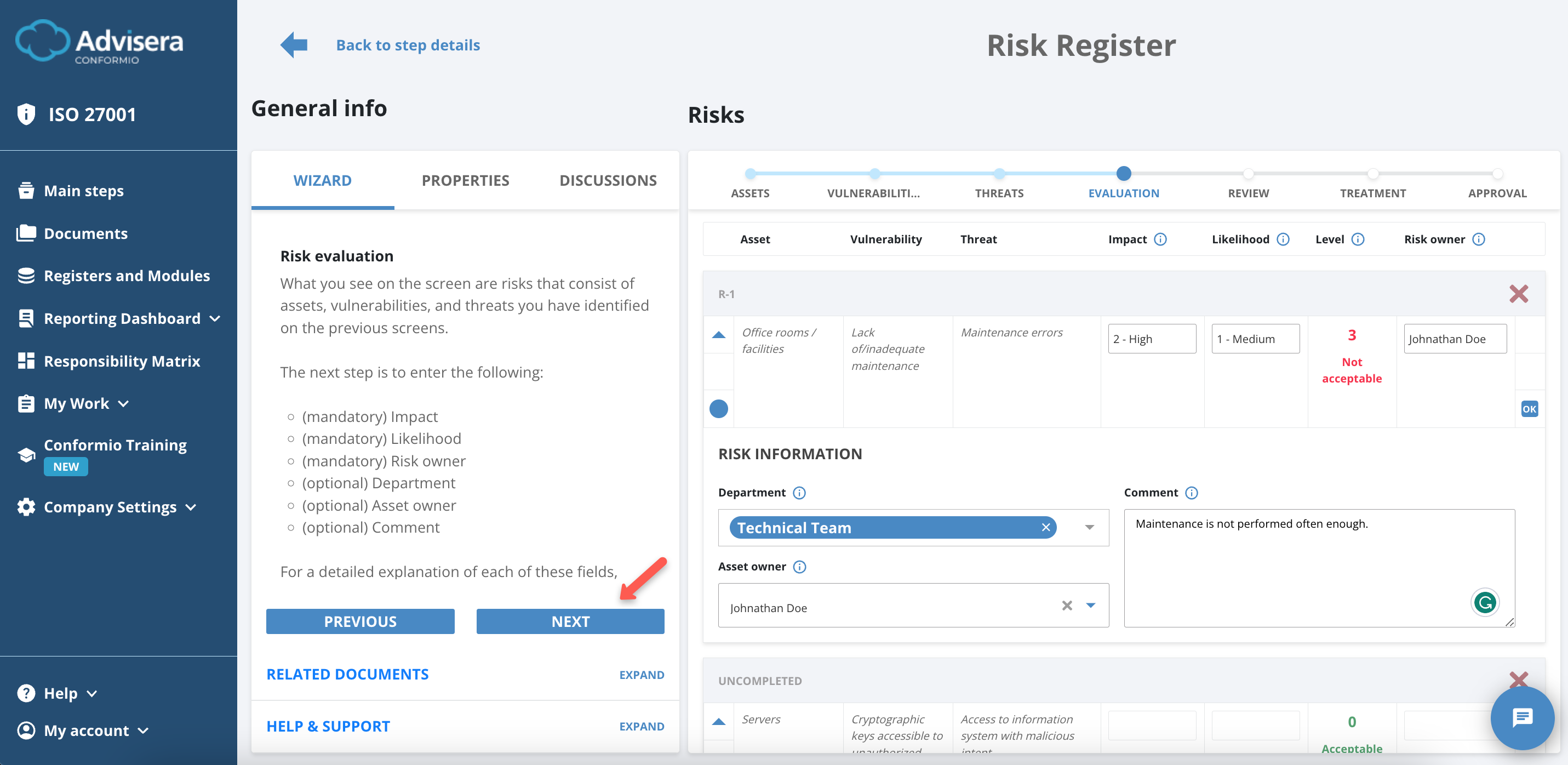
Evaluation
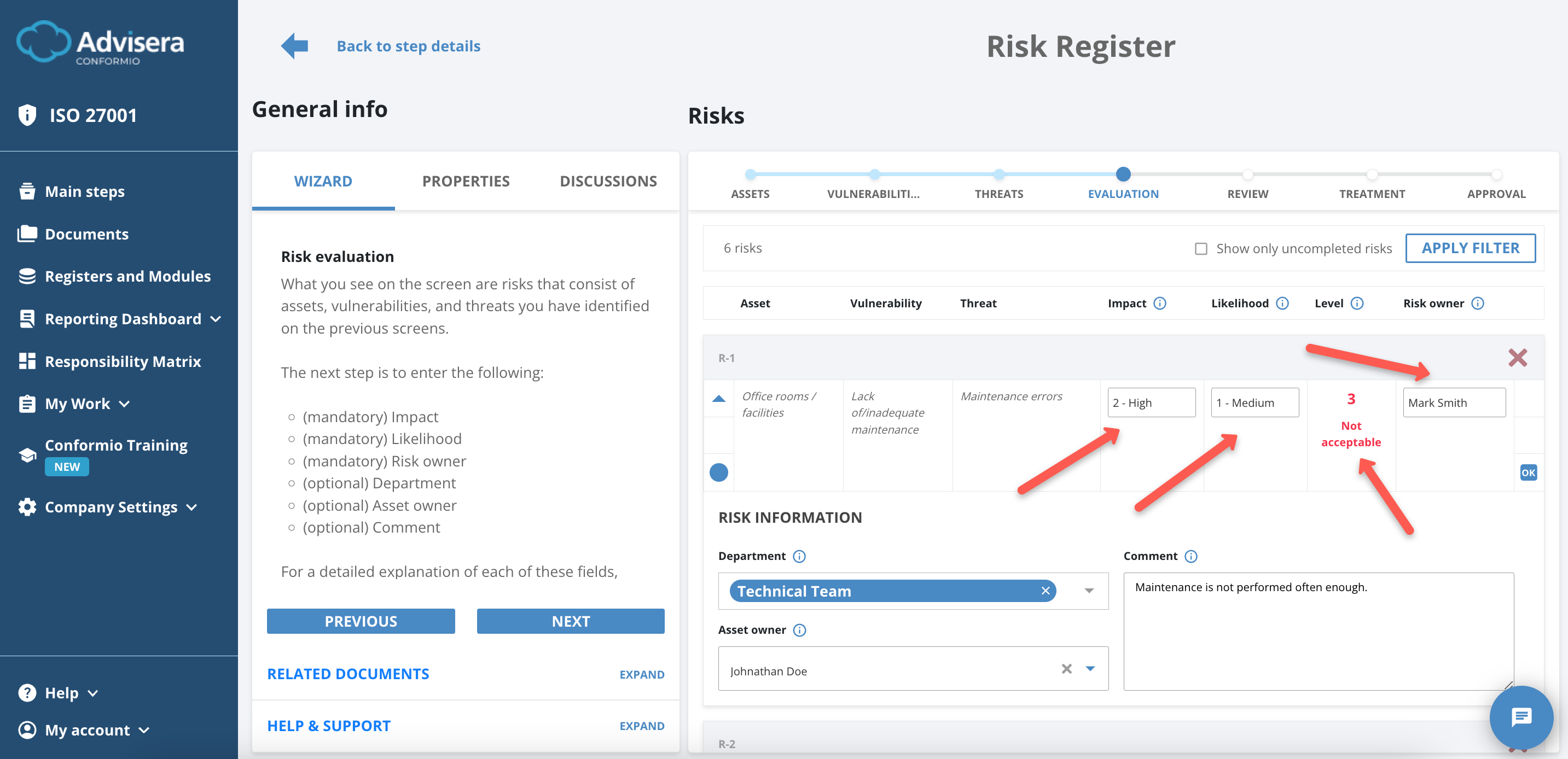
The Evaluation phase covers the selection of multiple values aimed at declaring the risks in your company as Acceptable or Not Acceptable, shown under the Level field and calculated by a 3×3 matrix.
Asset, Vulnerability, and Threat fields are non-editable as they were selected in the previous steps.
You have to input the Impact and Likelihood fields of the threat occurring.
Both variables are on a scale of 0 to 2:
- If impact and likelihood combined create a value above 2, the risk becomes Not Acceptable;
- If impact and likelihood combined create a value of 2 or below, the risk becomes Acceptable.
You have to select a Risk Owner – this is usually a person responsible for this asset. It is mandatory to select all the data up to this point.
If you have mistakenly selected a risk, you can discard it by clicking the X icon in line with the risk identification number R-000.
Unacceptable Risks
It is expected to have some unacceptable risks during your initial risk assessment. Any unacceptable risks will be lowered with selected controls in the Treatment step of the Risk Register.
Based on our experience, you will likely fail the certification audit without any identified unacceptable risks.
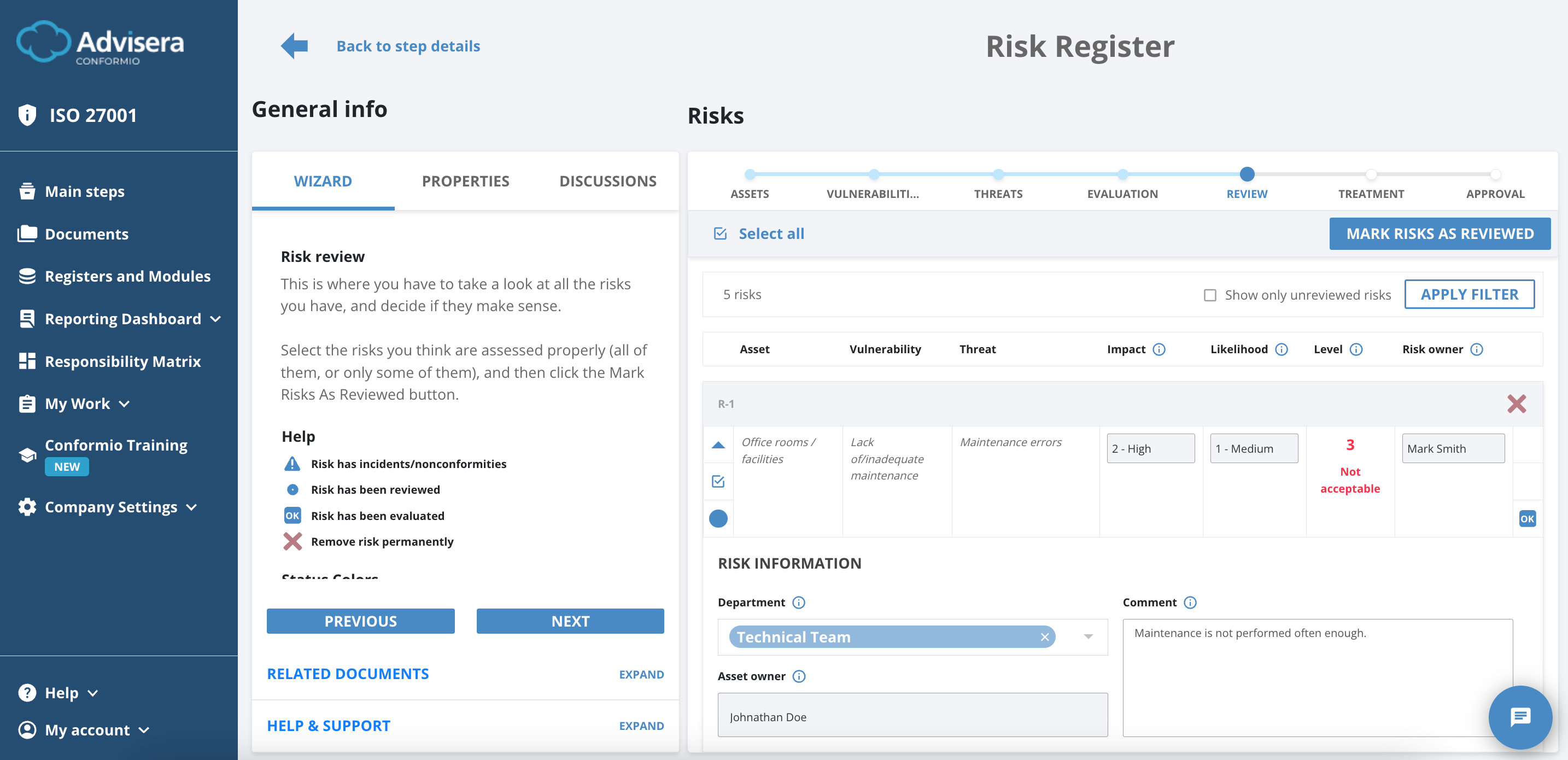
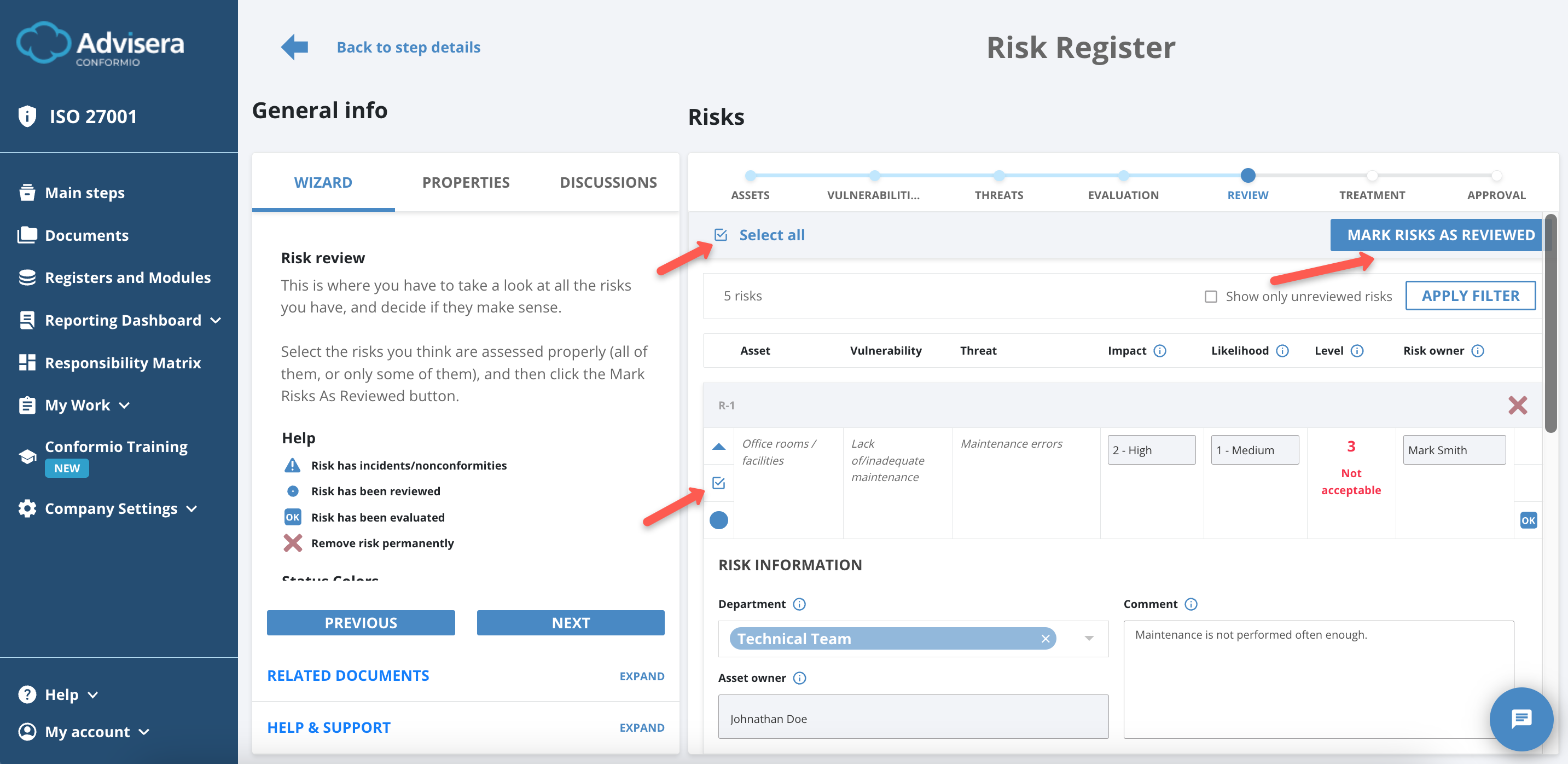
Review
In the Review step, you review all inputs in the risk Register until now and ensure the risk level values are properly evaluated.
After reviewing every risk, select all risks and click the Mark Risks As Reviewed button.
Note: This is the last time you can discard the risk.
After marking all risks as reviewed, click the Next button to proceed to the Treatment phase of the Risk Register.
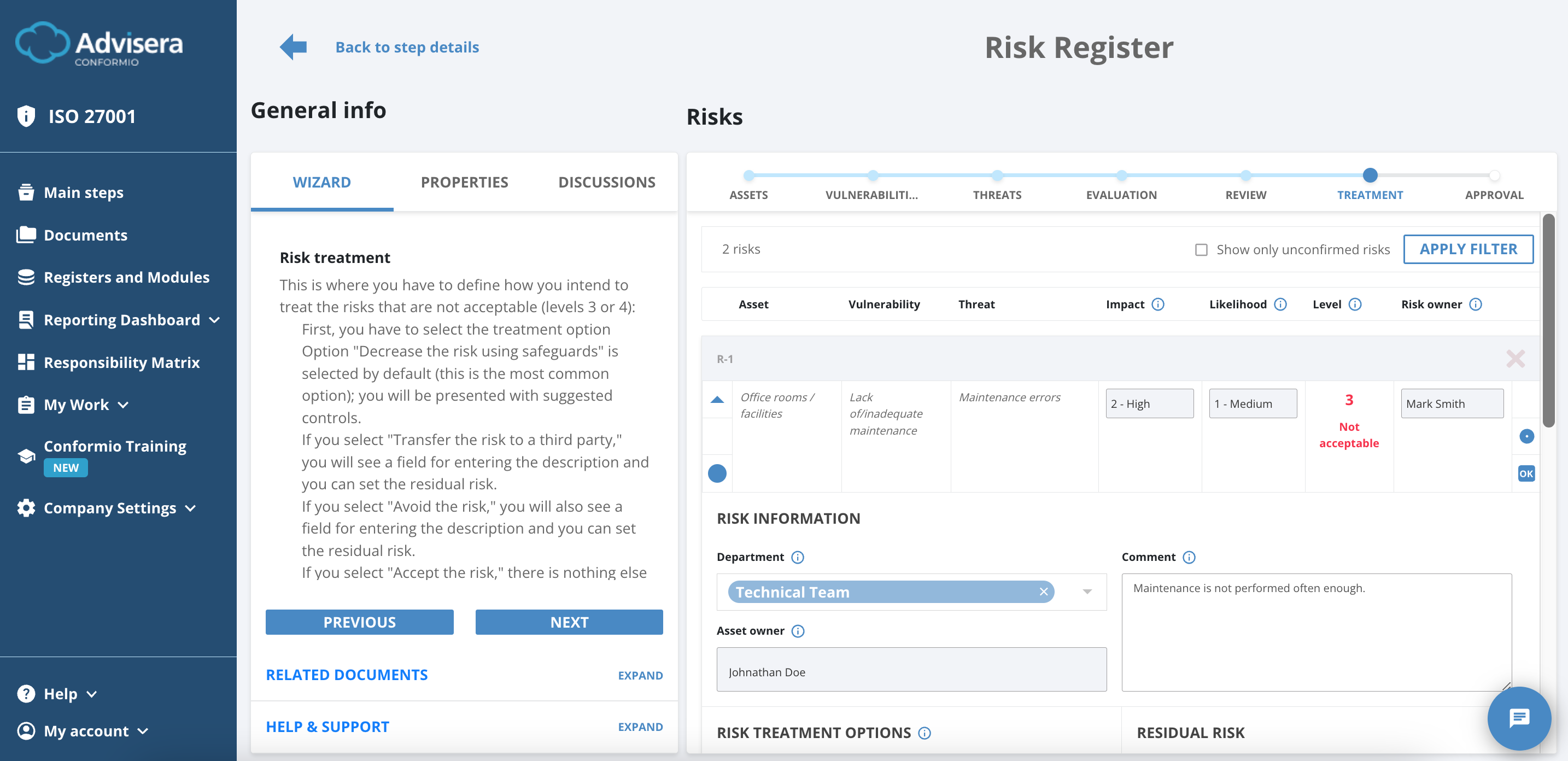
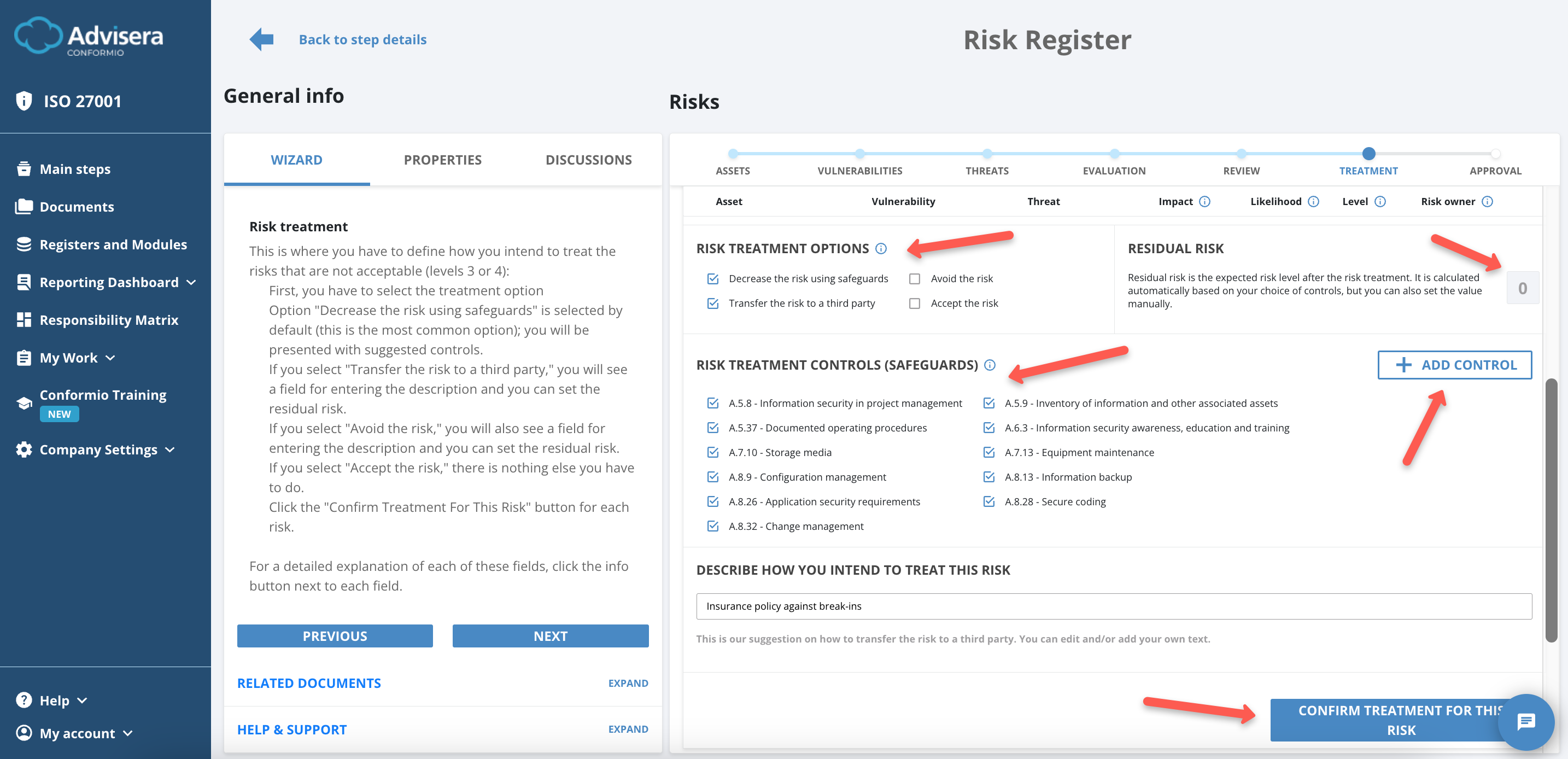
Treatment
During the Treatment step, you will only work with the Not Acceptable risks. For each unacceptable risk, you must select Risk Treatment Options to lower the risk.
Residual risk is what remains of the risk level value after the risk treatment options are selected.
There are four Risk Treatment Options available:
- Decreasing the risks using safeguards (controls);
- Avoiding the risk;
- Transferring the risk to a third party;
- Accepting the risk.
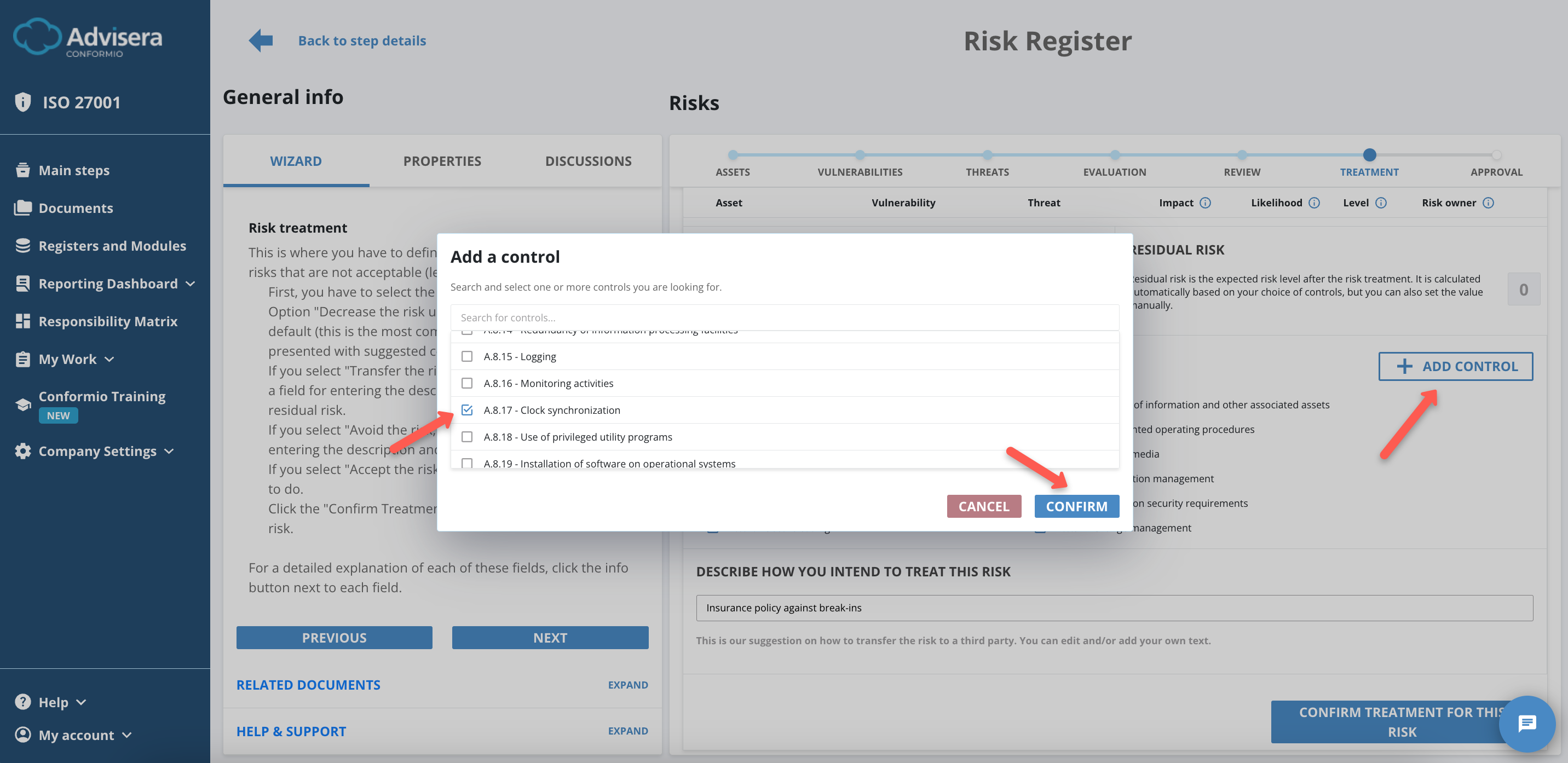
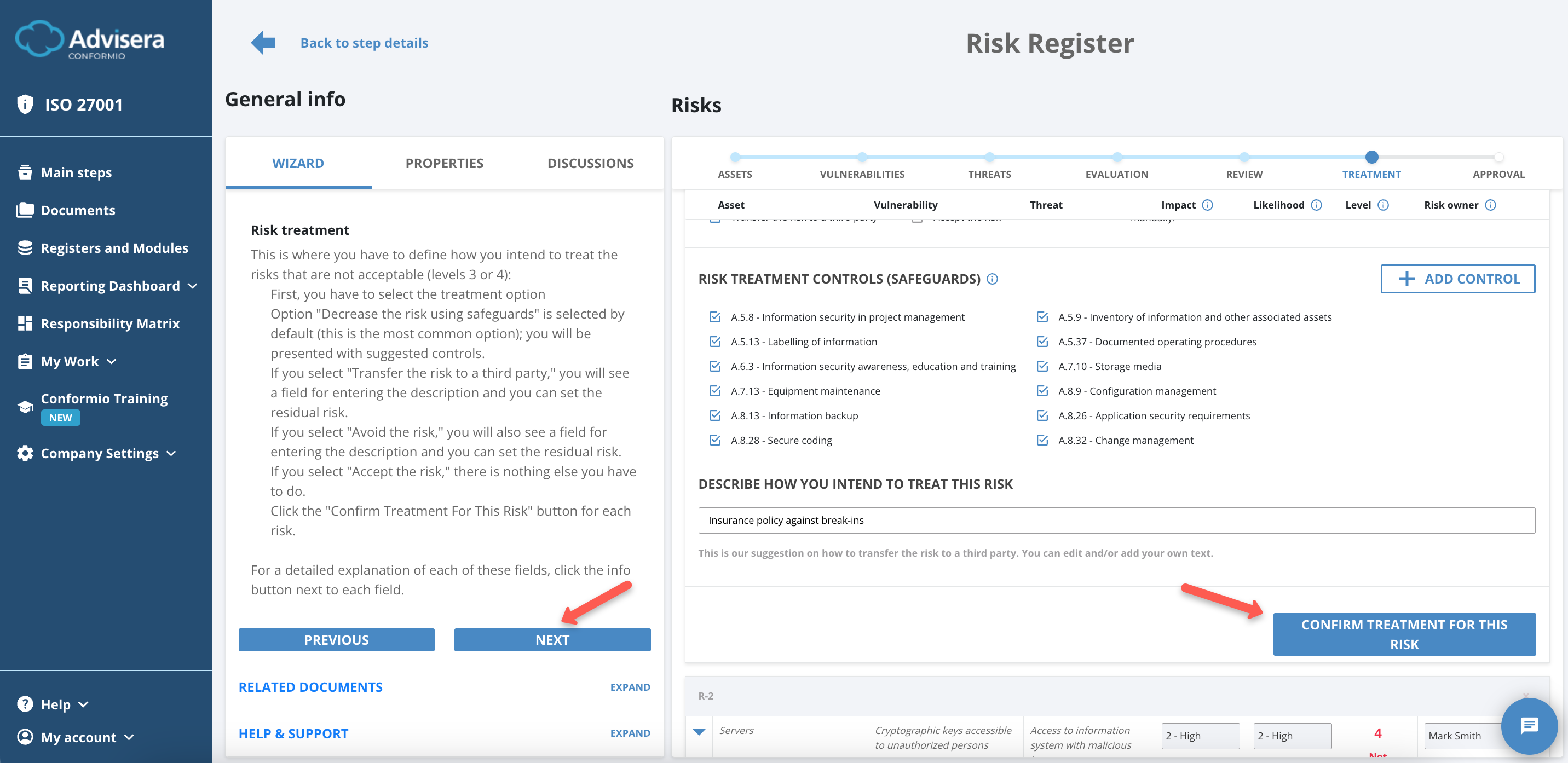
Risk Treatment Controls (Safeguards)
Risk Treatment Controls (Safeguards) are selections that help you decrease the residual risk. These controls are suggested based on our experience, and you can delete and/or add any controls you feel appropriate.
To add a control/safeguard do the following:
- Click the Add Control button;
- Find the appropriate control/safeguard from the list in a pop-up window opened;
- Click the Confirm button to add a control.
After you finish the risk treatment for a specific risk, click the Confirm Treatment for This Risk button.
After successfully lowering the risk for all risks and confirming treatment, click the Next button to proceed to the Approval phase of the Risk Register.
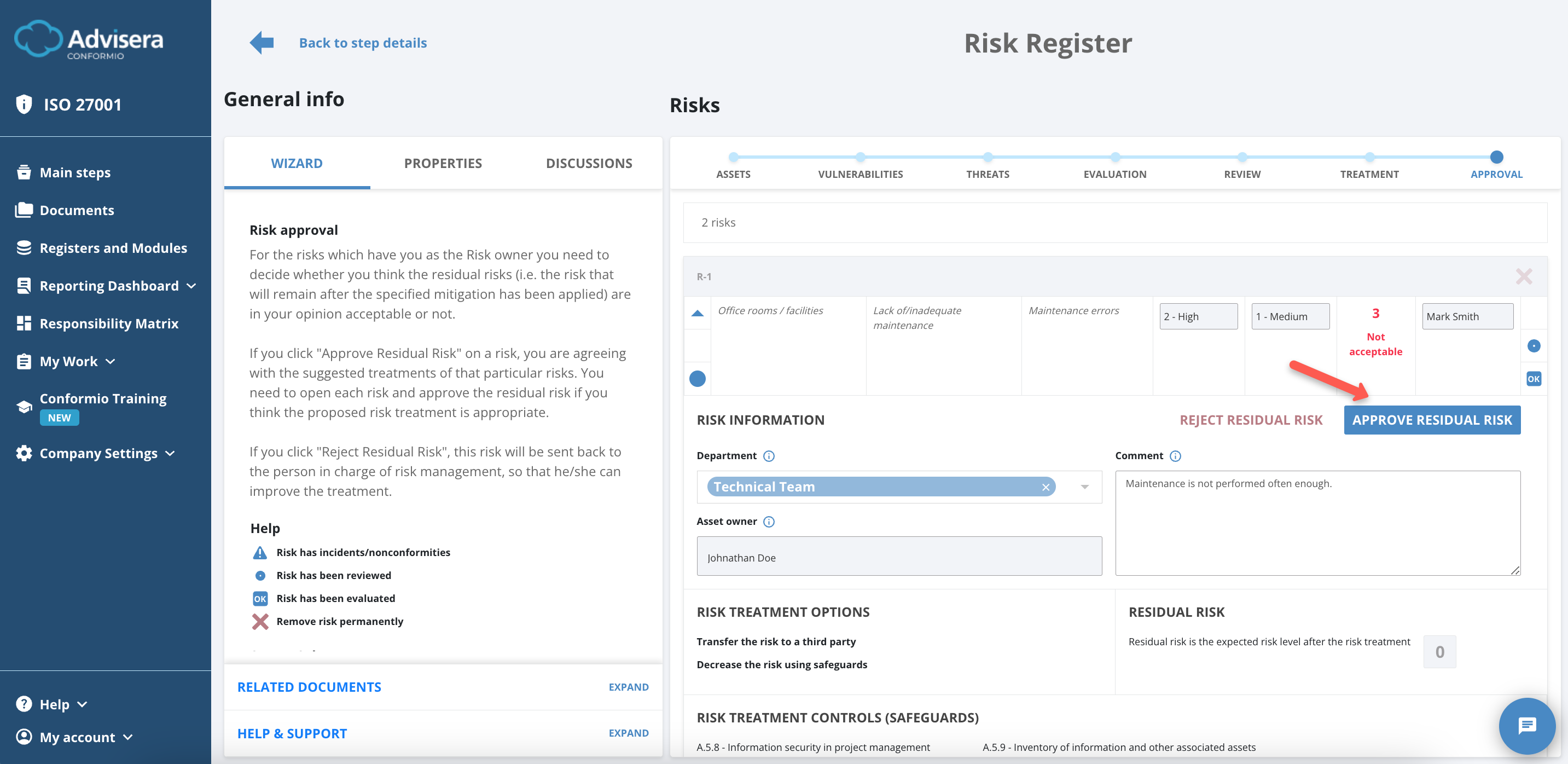
Approval
During the Approval step, the Risk Owners must:
- Approve the residual risk by clicking on the button Approve Residual Risk;
- Reject the residual risk by clicking on the Reject Residual Risk.
If you click Reject Residual Risk, this risk will be sent back to the person in charge of Risk Management to improve the treatment of said risk.
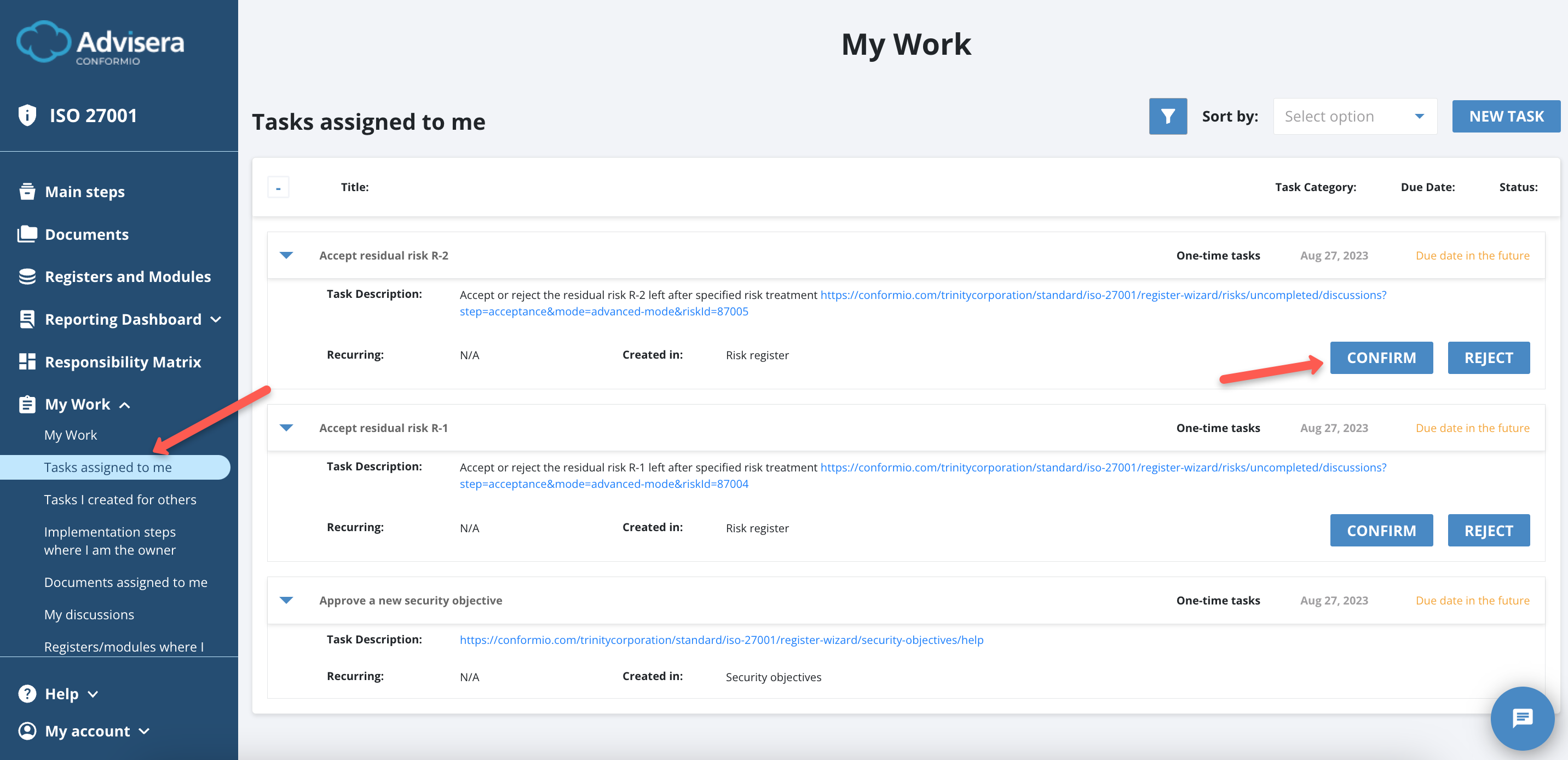
If you are a Risk Owner and also in charge of finishing the Risk Register, you can approve or reject residual risk.
If another person is the Risk Owner, they can reject or approve the residual risk through the My Work section.
Only when all risks are approved will the Risk Register be fully completed.
Completing Risk Register
After every risk treatment and residual risk is approved, the Risk Register will automatically complete itself.
By completing the Risk Register, two documents are generated:
- Risk Assessment and Treatment Report;
- Statement of Acceptance of Residual Risks.
Editing Risk Register
If you need to add more risks after the initial completion of the Risk Register, click the Edit Risk Register button and follow the steps from this article.
Frequently Asked Questions:
1. Can I manually edit the number of the Residual Risk?
Yes, that is possible by clicking on the number and replacing it with the desired number.
2. The button Next is not available to click. How to resolve this?
If the “Next” button is unavailable, something is missing from either of the steps in the Risk Register. Maybe you overlooked something. If you are sure everything is as it should be, please contact Conformio Support to provide a more in-depth look at the issue and possibly provide a resolution.
3. Can an Admin or Project Manager manually accept residual risk for specific risks?
No. If the admin or Project Manager are not actual risk owners of those risks, they cannot be accepted. Only the designated risk owner can accept the residual risk for those risks.